Introduction
Today, we find ourselves in a world that moves beyond standalone devices into a new technological age where virtually everything is connected. Machine Type Communication (MTC) can be defined as the ubiquitous and automated interaction of information between devices (computers, actuators, sensors, mobile devices, automobiles) without human intervention within a shared network, also called the Internet of Things (IoT) (Guo, 2021). This ubiquitous network collects information from the environments (i.e., interacts with the physical world). It provides information transfer services and emerging applications using the existing Internet infrastructure (Tello-Oquendo, Lin, Akyildiz, & Pla, 2019a). It is expected that by 2023 there will be 14.7 billion MTC connections worldwide (Cisco, 2020). The Third Generation Partnership Project (3GPP) has incorporated standards in cellular networks for MTC (3GPP, TR 37.868, 2011). For this reason, cellular networks such as Long-Term Evolution (LTE), LTE-Advanced (LTE-A), and fifth-generation (5G) networks have been considered suitable to provide connectivity for MTC, a technology called cellular IoT (CIoT). Among the main characteristics offered by the cellular network for this type of communication is having an adequate and well-deployed infrastructure that encompasses comprehensive coverage, large capacity, scalability, spectral efficiency, low latency, security solutions, and guaranteed Quality of Service (QoS) (Dakhilallah, Othman, Kamariah, & Mohd, 2020).
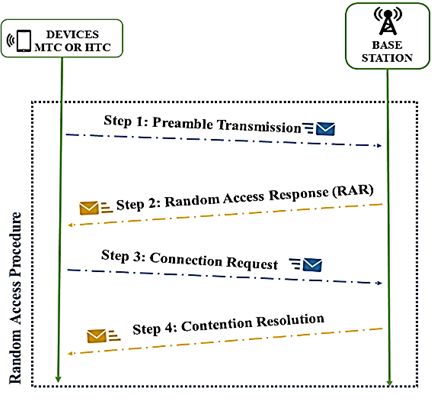
The diverse massive MTC (mMTC) services are electronic health care, electronic commerce, consumer goods, electronic transport, and control systems. These services will exhibit different traffic patterns, which combined with a large number of devices, makes the problem of resource allocation very challenging (Dutkiewicz, Costa, Kovacs, & Mueck, 2017), resulting in collisions and even the blocking of connection requests on the Random-Access Channel (RACH) (Kim, Lee, & Chung, 2018). However, not all devices are connected all the time. They may be just receiving data, transmitting it, or being in an idle state (Sahoo, Chou, Weng, & Wei, 2018). The standard mode for network access in cellular communications is through the random-access procedure, from now on RAP, based on contention (3GPP, TS 36.321, 2017). The device must perform this procedure as the first step in acquiring initial access to network resources. This procedure is performed through the RACH and consists of four stages: Preamble Transmission, Random Access Response (RAR), Connection Request, Contention Resolution.
According to 3GPP standards, a backoff procedure is performed in the event of an access failure or collision by a device, regardless of the cause (3GPP, TS 36.321, 2017). After this backoff procedure is finished, the device will start the RAP again. This backoff procedure computes a predetermined random time following a uniform distribution and the base station (BS) communicates it to the devices by system information blocks. A collided device must wait this time before retrying the RAP using a preamble. This time interval is called the backoff time (T BO ), and it is calculated based on an indicator called Backoff Indicator, from now on BI, whose value varies between 0 to 960 ms.
Most of the studies carried out regarding the evaluation of the RACH performance (Ouaissa, Benmoussa, Rhattoy, Lahmer, & Chana, 2016; Gursu, Vilgelm, Kellerer, & Reisslein, 2017), a fixed value is assumed for the BI parameter, generally 20 ms. However, the BI value may vary as specified in the 3GPP standards. Therefore, this research aims to assess the impact of BI variation and the benefits of a dynamic configuration in different massive traffic scenarios based on network performance metrics. Furthermore, the conducted evaluation applies to LTE / LTE-A and 5G networks, whose grant-based RAP is similar.
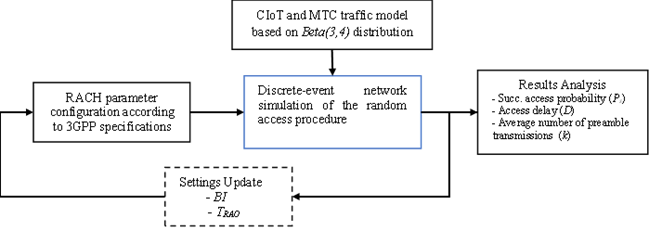
A discrete-event simulation model is devised using MATLAB software. The RAP is implemented, and the network performance is evaluated considering main metrics such as the probability of successful access, access delay, and the average number of preamble transmissions. Different mMTC traffic conditions are considered in the RACH by a traffic model that emulates massive communication environments. This allows analyzing the impact of the BI variation on the network performance through varying several RACH parameters.
Methodology
Overview and Theoretical Considerations
In cellular networks such as LTE / LTE-A and 5G, the standard mode for network access is via the contention-based RAP (3GPP, TS 36.321, 2017) that is performed in the RACH. This research evaluates the impact of varying the BI on the network performance through metrics such as the probability of successful access (Ps), the access delay (D), and the average number of transmitted preambles (k). The results are obtained through the configuration and variation of the RACH parameters, such as the periodicity of the random-access opportunities (RAOs), the BI, and massive traffic scenarios. These results allow determining a range of optimal BI values assuming reliability conditions based on the periodicity settings of the RAOs, from now on TRAO, for each massive traffic scenario, to comply with the 3GPP specifications (3GPP, TS 36.321, 2017).
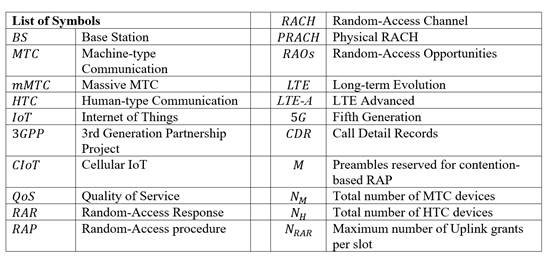
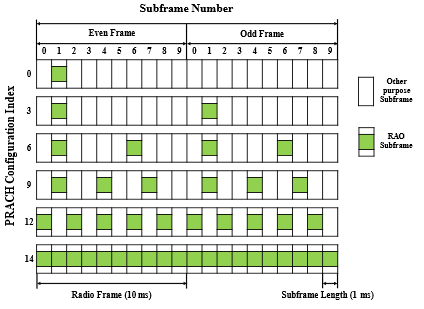
The contention-based RAP is performed through the RACH and consists of four steps: Preamble transmission, Random Access Response (RAR), Connection Request, and Contention Resolution, as illustrated in figure 1 (Tello-Oquendo, et al., 2018a). The periodicity of the RAOs, T RAO , is periodic sequences reserved in the uplink channel to transmit access requests to the network. That is determined by the PRACH configuration index (prach-ConfigIndex) (Pacheco-Paramo & Tello-Oquendo, 2020). Downlink and uplink transmissions are organized into radio frames of 10 ms each. Each frame is divided into ten equally sized subframes. The duration of each subframe is 1 ms. Moreover, each subframe is further divided into two equally sized time slots; each slot is 0.5 ms. There is a total of 64 PRACH configurations available, starting from a minimum periodicity configuration of one RAO for every two frames (every 20 ms) to a maximum of one RAO for each subframe (every 1 ms) (3GPP, TS 36.211, 2020), as can be seen in figure 2.
The backoff process is a collision control technique in the RACH, proposed by the 3GPP standards in case of failure in access to the network (3GPP, TS 36.321, 2017). This control technique is performed within the contention-based RAP. This procedure is applied to all the devices that failed in the first attempt to access the network. After that, devices must wait a predetermined time before retrying the RAP and be able to retry a preamble transmission at the next available RAO. This time is known as the backoff time, TBO (ms), and it is chosen randomly by the UEs according to equation (1):
( 1 )
where 𝒰() means uniform distribution, BI is the backoff indicator defined by the BS, and its value varies from 0 to 960 ms. The BI value is sent in the RAR message (step 2), which is read by all devices that sent a preamble in a previous RAO. That means that each device that did not obtain confirmation with the RAR is considered a failed attempt (a collision originated). Then, it uses the BI to compute the TBO before attempting to start from the first step again (Vidal, Tello-Oquendo, Pla, & Guijarro, 2019). In the same way, it happens with the devices that do not receive the contention resolution message (step 4), which guarantees successful access to network resources. They compute the TBO before making another attempt, starting again from the first step. Figure 3 illustrates how the backoff procedure is applied in the RACH when a collision occurs in the steps mentioned above, respectively.
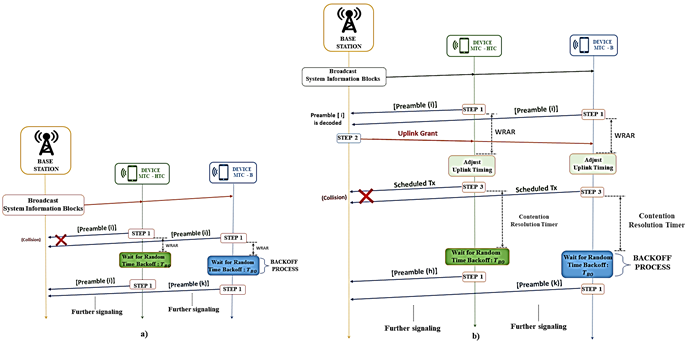
Figure 3: Description of backoff procedure. a) Collision in the first message when multiple devices use the same preamble (preamble (i)) and it is not decoded; the backoff time is applied to make a new attempt. b) Collision in the third message when multiple devices use the same uplink physical resources; the backoff time is applied to make a new attempt.
System Model
A discrete event simulation model was implemented in MATLAB software. The procedure followed for the analysis is contemplated in five blocks, as described in figure 4. The system model assumes a single cell or BS where both MTC and Human Type Communication (HTC) devices coexist. That allowed obtaining the different network performance metrics considering background HTC traffic. The value of each performance metric is obtained as the mean of 100 simulation runs. Each simulation run uses a different random seed and ends when all the UEs have completed their random-access procedure. The RAP, jointly with the traffic model, is characterized in the “CIoT and MTC Traffic Model” block. MTC traffic will use the model described in the specification (3GPP, TR 37.868, 2011), which follows a Beta distribution of parameters (3,4) for 10 seconds. For HTC traffic, the studies (Tello-Oquendo, Pacheco-Paramo, Pla, & Martinez-Bauset, 2018b) were taken as a reference, where they describe that HTC traffic follows a uniform distribution over time. This traffic is based on data provided by the Call Detail Records (CDR) granted by the telecommunications company “Telecom Italia,” whose average rate of access requests arrivals per second was 55 during 10 min time.
Table 1 lists the parameters used throughout our evaluation and analysis. We assume two PRACH configurations. The typical one, using the prach-ConfigIndex6, whose TRAO = 5 ms. The second one, using the prach-ConfigIndex14, whose TRAO = 1 ms.
Table 1: Configuration of the random-access channel parameters.
| Parameters | Configuration |
|---|---|
| Total number of devices MTC 𝑁 𝑀 | 10000, 15000, 20000, 25000, 30000 |
| Total number of devices HTC 𝑁 𝐻 | 33000 |
| Setting the PRACH Index (prach-ConfigIndex) | 6, 14 |
| RAOs periodicity 𝑇 𝑅𝐴𝑂 | 5 ms, 1 ms |
| Subframe Length (Subframe length) | 1 ms |
| Preambles reserved for contention-based RAP 𝑀 | 54 |
| RAR window size 𝑊 𝑅𝐴𝑅 | 5 subframes |
| Maximum number of Uplink grants per subplot 𝑁 𝑅𝐴𝑅 | 3 |
| Maximum number of preamble transmission attempts ( 𝑘 𝑚𝑎𝑥 ) | 10 |
| Backoff indicator (𝐵𝐼) | (20 a 960 ms) variable |
| Contest Resolution Timer | ubframes |
Performance Metrics
Successful access probability
The variable Ps denotes the successful access probability, and it is defined as the relationship between the devices that successfully complete the contention-based RAP and the total number of devices that entered the BS during the simulation time, as described in equation (2).
(2)
where 𝑛 𝐴 is the total number of MTC devices with successful access and 𝑛 𝑇 is the total number of MTC devices that entered the BS.
Access delay
It is denoted by variable D, and it is the time elapsed between the first access attempt (preamble transmission) and the successful completion of the RAP, also considering the delay generated by the BI, which is a function of the number of attempts made until obtaining successful access. We start from a cumulative distribution function (CDF) described in equation (3). This equation is used to obtain a probability distribution based on the delay generated by each device after getting successful access to the network and the total number of devices that completed the RAP, as follows:
(3)
where 𝑝 𝐷 (𝒏;𝒎𝒔) is the cumulative probability of “𝑛” delay expressed in ms and 𝑀 𝐴 ( 𝐷 (𝒏;𝒎𝒔) ) is the set of MTC devices that obtained successful access in “n” time delay. The 95th percentile is used for this metric since this percentile is closer to the maximum delay generated.
Average number of preamble transmissions
It is defined by the variable 𝑘 and is the statistic of the number of transmissions that a device uses a preamble until it can complete the RAP after its first failed attempt. To evaluate this indicator, a CDF is first applied, described in equation (4), for each of the transmitted preambles until the maximum number of attempts is reached ( 𝑘 𝑚𝑎𝑥 ).
(4)
where 𝑝 𝑘 𝑛 is the cumulative probability of “𝑛” preamble transmission, 𝑀 𝐴 ( 𝑘 𝑛 ) is the set of MTC type devices that successfully accessed the network in “n” preamble transmission. Once the different probability data have been obtained, as the next step, the weighted arithmetic mean is used, as described in equation (5), to calculate the mean or average value of the number of transmissions necessary to successfully carry out the RAP and obtain access to the network. This value will depend on the maximum number of preamble retransmissions that is set ( 𝑘 𝑚𝑎𝑥 )
(5)
where 𝑘 𝑛 is the transmitted preamble number and 𝑁 is the sum of the accumulated probabilities in the different preambles.
Results
This section presents the simulation results to evaluate the impact that the different BI values cause on the performance of the RACH based on the RAOs periodicity settings, the different massive traffic scenarios, and the performance metrics mentioned above. Figure 5a and figure 5b depict the successful access probability for the prach-ConfigIndex configurations 6 and 14, respectively.
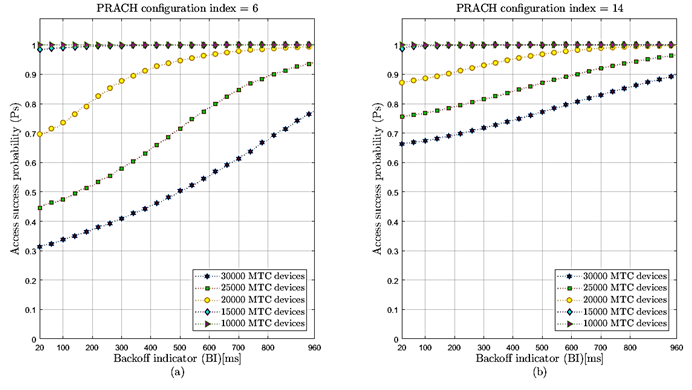
Figure 5: The successful access probability 𝑃 𝑠 based on different massive MTC traffic scenarios with different BI values (20 to 960 ms). a) Random access opportunity periodicity setting of 5 ms (prach-ConfigIndex6). b) Random access opportunity periodicity setting of 1 ms (prach-ConfigIndex14).
For the most critical scenario (30000 MTC devices), on the one hand, when the maximum BI value is used (960 ms) with TRAO=5 ms, a successful access probability of 77% (Figure 5a) is reached. On the other hand, when the maximum BI value with TRAO = 1ms is used, a successful access probability of 89% is achieved (Figure 5b).
The access delay based on the 95th percentile for the 6 and 14 prach-ConfigIndex configurations in the different massive traffic scenarios are shown in figure 6a and figure 6b, respectively. This performance metric indicates that the BI value is directly proportional to the delay generated; the higher the BI value, the greater the delay caused. For example, when making a comparison based on the most critical mass traffic scenario (30000 MTC devices), it was determined that when TRAO = 1ms is used, a lower delay (around 8.98% less) is achieved compared to the configuration with TRAO = 5ms. Then, it is suggested to use the prach-ConfigIndex = 14 (i.e., TRAO = 1ms) when the traffic load in the RACH is high.
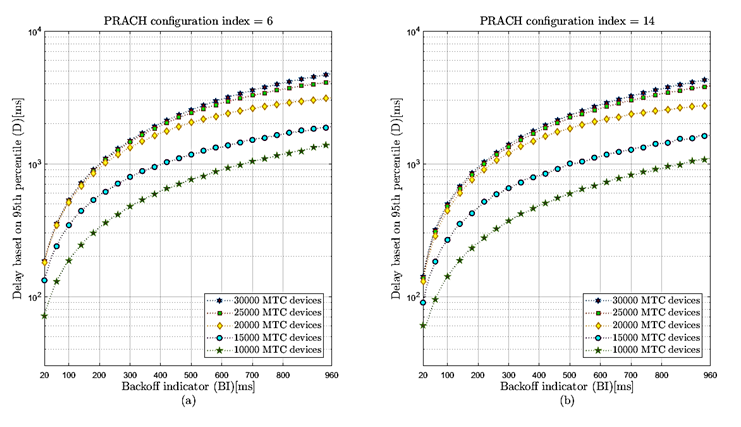
Figure 6: Access delay (𝐷) based on the 95th percentile for the different massive traffic scenarios. a) Random access opportunity periodicity setting of 5 ms (prach-ConfigIndex6). b) Random access opportunity periodicity setting of 1 ms (prach-ConfigIndex14).
The average number of preamble transmissions for the prach-ConfigIndex configurations 6 and 14 under different massive traffic scenarios are shown in figure 7a and figure 7b, respectively. This performance metric indicates the number of attempts made by devices that successfully access the network. The range used for transmissions is 0 to 10, the latter being the maximum number of possible preamble retransmissions. The number zero indicates that a device was successfully accessed on the first attempt and did not retransmit.
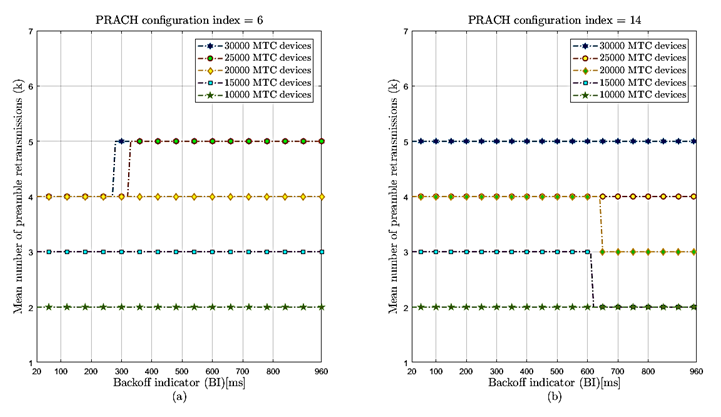
Figure 7: Average number of preamble transmissions (k) under different massive MTC traffic scenarios. a) Random access opportunity periodicity setting of 5 ms (prach-ConfigIndex6). b) Random access opportunity periodicity setting of 1 ms (prach-ConfigIndex14).
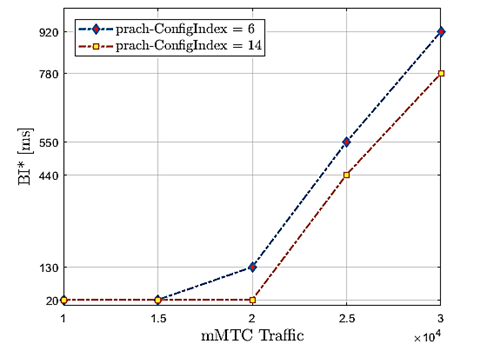
Based on the results presented above, two reliability conditions were assumed based on the successful access probability and the most critical massive traffic scenario (30000 MTC devices) to determine an optimal range of BI values, which guarantee the connectivity of the devices to the network. The first condition will be for all BI values that obtain a successful access probability greater than 75% when working with TRAO = 5ms (standard set). The second condition will be for all BI values that obtain a probability of successful access greater than 85% when working with TRAO = 1ms. Figure 8 illustrates the minimum value of the backoff indicator that meets the reliability condition called BI* for each RAO periodicity configuration in each massive traffic scenario.
As can be observed in figure 8, when a configuration of prach-ConfigIndex = 14 𝑇 𝑅𝐴𝑂 =1 𝑚𝑠 is used, a broader range of massive traffic scenarios can be supported, and this is understandable because the devices use all the frames to transmit, unlike when using a setting of prach-ConfigIndex = 6 𝑇 𝑅𝐴𝑂 =5 𝑚𝑠 . These results show how the performance in the cellular network could be affected when handling massive traffic, particularly in the access delay. The determined ranges will be crucial for future research to dynamically determine the optimal BI value around the massive traffic level connecting to the BS.
Discussion
The binary exponential backoff (BEB) technique discussed in Kwak, Song, & Miller (2005) is a frequently used collision resolution mechanism. Kwak, Song, & Miller (2005) presents analytical findings on throughput and medium access delay. Fan, Gao, Wang, & Dong (2008) apply theoretical analysis to evaluate the performance of a different type of backoff algorithm in IEEE 802.11 ad hoc networks. Finally, Zhang & Liu (1993) employed recursive formulas to examine the multi-channel slotted Aloha algorithm to determine the probability of packets being successfully transported via parallel channels.
On the other hand, many studies have been conducted to alleviate RACH congestion under massive access scenarios. However, the backoff approach for RACH collision resolution has been studied moderately. Seo & Leung (2011) examine multi-channel slotted Aloha algorithms in the context of LTE and IEEE 802.16 based systems, combining the ideas introduced in Kwak, Song, & Miller (2005) and Zhang & Liu (1993). In addition, Seo & Leung, (2011) implies that at least one packet is sent in each slot. This assumption is no longer valid under low traffic conditions, such as those found in LTE (3GPP, TS 36.211, 2020). Therefore, tolerating the vast access of M2M communications necessitates optimizing cellular networks’ standard backoff mechanism.
This article studied the backoff procedure as a control technique to deal with collisions originating in the random-access channel (RACH) with massive traffic. In addition, the impact produced by varying the backoff indicator (BI) concerning the configuration of the periodicity of RAOs was explored for different massive traffic scenarios. The successful access probability was assumed to be the primary performance metric. Therefore, the study focused on characterizing the BI values that meet the reliability conditions for both RAOs periodicity configurations [5 ms (prach-ConfigIndex = 6) and 1 ms (prach-ConfigIndex = 14)]. As a result, an optimal range of BI values has been characterized for each type of massive traffic scenario entering the BS. This range would allow compliance with the provisions of the 3GPP standards corresponding to the random choice of a backoff time.
The value of BI has a significant impact on the RACH’s overall performance. A small BI value, for example, permits devices to retry access after a short time, thereby increasing the number of collisions during burst arrivals. A high value of BI, on the other hand, may increase the successful access probability at the expense of access latency. As a result, finding the appropriate BI value that maximizes access success probability while maintaining a reasonable access delay is critical.
Conclusions
An evaluation study was conducted to analyze the impact of the BI variation on network performance metrics such as the probability of successful access, access delay, and the average number of preamble transmissions under different mMTC traffic conditions using a discrete-event simulation model. A comparison was made considering the most suitable configuration for the different massive traffic scenarios evaluated using the critical configuration parameters of the RACH. An optimal range of BI values was determined through reliability conditions that will comply with the provisions of the 3GPP standards.
It was observed that for the massive traffic scenarios of 10000 and 15000 MTC devices, any of the two RAOs periodicity configurations could be implemented since both cases obtain a Ps ≥ 0.98; while, for other massive traffic scenarios, the TRAO = 1ms setting should be used, since it has a higher optimal BI range and a Ps ≥ 0.85. The performance metrics were also compared in the most critical massive traffic scenario evaluated. The RAOs periodicity setting of 1 ms was the most appropriate due to the better results obtained, and it can be incorporated in delay-tolerant applications.
In conclusion, the access delay is increased to have a reliable transmission without incorporating control techniques and considering only the backoff procedure-consequently, the number of preamble transmissions increases. Therefore, using these types of solutions is reasonable in delay-tolerant applications. This research can be used as a starting point for future studies in which it is proposed to use mechanisms to update the backoff time dynamically based on the mMTC traffic that enters the BS. These mechanisms can be implemented using machine learning so that the network can adapt to stringent QoS requirements.
Authors’ contributions
In accordance with the internationally established taxonomy for assigning credits to authors of scientific articles (https://casrai.org/credit/). The authors declare their contributions in the following matrix: