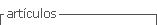1. Introduction
The implementation of wireless sensor networks (WSN) based on the IEEE 802.15.4 link protocol (Gallegos & Noguchi, 2019, Feb. 17-20), in conjunction with network protocols like 6LoWPAN (Yang et al., 2019), ZigBee (Mahlknecht et al., 2016), it has allowed increasing the number of applications in various areas, such as home automation (Abella et al., 2019), farming (Sharma et al., 2019), health (Adame et al., 2018), traffic monitoring (Vachan & Mishra, 2019, April 12-15), forest fires (Kadir et al., 2019, Oct. 2-4) and industrial areas (Queiroz et al., 2017), due to the low cost and ease of implementation. The internet of all things (IoT) is one of the technological trends that is being adopted with more force today, which uses several communication technologies, one of them is the Wireless Sensor Network (WSN) which are characterized by being made up of sensor nodes that operate with batteries and with low computing capacity (Sharma et al., 2020).
Wireless sensor networks have limited resources (Srivastava et al., 2018, Oct. 3-4) and therefore need to be designed efficiently to facilitate their deployment and configuration. Furthermore, due to a large number of sensor nodes, the self-configuration of the network is a technological challenge (Kobo et al., 2017). Unfortunately, in a network that contains a large number of nodes, the address allocation processes (Lakshmi et al., 2018, Jan 10-12), as well as the formation of the topology, take a large amount of time. Within the network with a small number of sensors, the administrator can easily assign addresses. However, as the number of nodes increases, this way of assigning them is not appropriate and therefore an automatic configuration is necessary.
Automatic configuration in a WSN (Dinh & Kim, 2019) is a name for proposals characterized by an automatic assignment of addresses to the nodes, as well as for the automatic definition of the network topology. The experiences obtained have determined that self-organization, self-configuration to have automatic connectivity and connection to the Internet, is an important research topic in large scale wireless sensor networks.
In general, this type of configuration is implemented in one node and then the other nodes in the network are automatically configured. These mechanisms are easy to use, have a quick deployment and are energy efficient (More & Raisinghani, 2017). Regardless of the area in which wireless sensor networks are used, it is necessary for the nodes to have a global address on the network that facilitates the sending and receiving of data, and the route by which the data can reach their destination, tasks that are performed by network protocols such as 6LowPAN and Zigbee.
With hundreds or thousands of nodes the processing times to assign identifiers and define the topology are high especially when it comes to multi-hop networks. In these cases data transmission may to have great delays due to paths that have a large number of hops (Chughtai et al., 2017).
The high times to have the large-scale wireless sensor network self-configured and ready to use, are basically due to the low processing capacity of the nodes, which makes it impossible to reuse network routing protocols. Internet, causing the emergence of standards like 6LowPAN which is an adaptation of the IPv6 protocol. In other cases, routing protocols on a wireless sensor network are proprietary to manufacturers.
Sensors nodes can be partitioned into multiple clusters to employ techniques that reduce the size of the network and simplify routing decisions and reduce the processing delay on the node. These techniques divide nodes into clusters, each having a designated cluster head that computes local routing decisions among sensors within its own cluster (Curry & Smith, 2016) and the data originating at nodes located at nodes in a routing tree may require a large number hops for end to end transmission.
Our proposal consists of verifying that only using the link level processes, specifically the IEEE 802.15.4 protocol, it is possible to automatically assign global addresses to the nodes (Egas et al., 2016, Nov. 15-17) and generate the wireless network topology of multi-hop sensors, which allows end-to-end connectivity within the network, without using network-level processes (network protocols), so that the identifiers assigned by the link-level not only serve for communication between contiguous nodes, but also for communications between source node and destination node in the personal wide area network. The use of the link-layer to define the network topology, as well as assigning global addresses to the nodes, reduces the processing delays at the node and also optimizes energy consumption due to the fact that the processes to be carried out are reduced at the node.
Since experimenting with wireless sensor networks began, there has already been a debate about the relevance that a wireless sensor network should replicate the layered structure of the Internet or if it should have a more flexible design taking into account the characteristics of nodes that have low computing capacities and work with batteries
We consider that removing the network layer from the architecture of wireless sensor networks is appropriate, given that up to now there are two trends to define its architecture, the first one that tries to follow the layer-model of the architecture of the Internet, a proposal that is limited by the processing capacity of the nodes, and the other trend in which the architecture is directly associated with the applications (Kumar et al., 2014).
Our work is essential to facilitate the deployment of simple and cheap WSNs, pave the way for the implementation of new services and EoT applications (Torres-Ruiz et al., 2018) and take advantage of new paradigms such as fog computing (Rahbari & Nickray, 2019), cloud computing (Dwivedi & Kumar, 2018, Nov. 2-4) and the analysis of large amounts of data (Kim et al., 2019) also in WSNs.
The validity of our proposal was checked on a prototype of a wireless sensor network, using development software that allows the IEEE 802.15.4 standard frames to be manipulated directly without the need to load an operating system on the nodes. The algorithm is executed in each node and the verification of the operation is carried out in several test scenarios using a network prototype. In this context, our proposal generates the following contributions:
- Automatically assigning global addresses at the link-layer, which are also used as network-layer identifiers using the IEEE 802.15.4 protocol.
- Tree topology creation for a multi-hop wireless sensor network using the IEEE 802.15.4 protocol.
- Decreased network autoconfiguration time.
2. Related work
In general, self-organization is the process of autonomy and formation of connectivity, addressing and routing (Hilmani et al., 2018, April, 23-24) which is limited by the characteristics of the sensor nodes. Different methods have been developed for autoconfiguring addressing in a WSN. In (Mavani & Asawa, 2019, Aug. 8-10) work studies, the effect of node wake-up frequency on the address configuration latency of IPv6 addressing deploys periodic pseudo-random IPv6 addressing scheme for low power 6LoWPANs to achieve privacy of the sensor nodes
An addressing scheme based on multi-hop clusters and aims to reduce addressing cost and delay in 6LowPAN is proposed in (Dou et al., 2017). Each node employs beacons to obtain a unique address from a neighbor node. A cluster covers a multi-hop area, so the frequency of a sensor node performing the addressing is lowered and the total addressing cost and delay are reduced.
In (Wang et al., 2018) A hierarchical addressing scheme for 6LoWPAN is proposed in order to aim to reduce the addressing cost and latency. The proposed scheme includes the addresses of initialization and addresses maintenance algorithms. Each sensor node can be configured with a globally unique address without duplication address detection. After the address initialization process ends, a new node obtains a globally unique address. Released addresses are recovered for reuse so that there are enough address resources available.
In (Deshpande & Shankar, 2016, March, 4-6), a discrete cluster-based addressing scheme for WSNs based Internet of Things paradigm has been proposed. The authors propose to form clusters of wireless sensor nodes based on the type of application in sensor nodes. A unique address is assigned to every cluster and the sensor nodes.
Examples of routing protocols used by this technique are routing protocols for hierarchical networks called LEACH (Singh et al., 2017) which uses localized coordination and control for cluster formation and operation. In this protocol sensors elect themselves to serve as the cluster head based on residual energy levels among neighboring sensors nodes, PEGASIS (Ghosh et al., 2016, Feb. 25-26) is a proactive Hierarchical Routing protocols, the deployed nodes, forms a chain. Each node in the chain fuses its own data to the data received from its predecessor and sends the aggregated data to its successor along the chain except the terminal nodes.
In (Al-Dulaimy & Frey, 2019, Sept. 11-13) a approach to efficiently manage a software-defined wireless sensor networks is proposed by means of a hierarchical addressing scheme. It is based on a tree of address masks which are used to split the network into subnets. Each subnet is assigned a range of host addresses and a subnet header that is used as a gateway to its children. The sensor nodes need only to recognize the subnet where a packet is destined to and forward that packet to the subnet gateway.
Finally, it is necessary to mention the AODV protocol (Zrelli et al., 2019, Sept. 19-21) used by ZigBee, in case of knowing the network address, the link-layer address is requested using unicast. If not, it is requested by broadcast. ZigBee edge devices respond to these requests with their own addresses, while ZigBee routers and coordinators also send the addresses of all devices associated with them. Two addressing modes are used. On the one hand, direct addressing uses the radio address and the end node number, on the other hand, indirect addressing requires all relevant information and sends it to the network coordinator. In all the previous cases, the network address that allows end-to-end connectivity uses routing protocols, in order to preserve the paradigm of the internet architecture, however, due to the processing limitations of the sensor nodes, it is impossible to replicate Internet protocols in wireless sensor networks.
2. Methodology
The wireless sensor network is divided into a cluster, and each cluster is made up of a cluster Head. The network, Figure 1, is connected to the Internet through an access router (AR), the AR node and all the cluster header nodes form a tree where the root is AR, routing can be accomplished using hierarchical identifiers for each node, without storing routing information or setting routing.
In stateful address allocation schemes, cluster header nodes maintain allocation states to determine the availability of addresses to assign to a new node that connects to the network. A hierarchical assignment guarantees the assignment of unique global addresses. The group leader is only responsible for assigning addresses to the members of her cluster.
When a node requests an address from the cluster manager to join the tree topology network, acceptance of this request will depend on the availability of addresses for that group, therefore, the scalability of the network is limited by the number of free addresses to assign in each group. To overcome this limitation, we make use of the speed with which addresses are reassigned to the entire network because, in this case, the cluster manager does not have addresses to assign requests to his cluster manager (node that assign an address), reassign the addresses again to take into account the new nodes entered.
The IEEE 802.15.4 standard uses two types of addressing: short (16-bit) addressing and extended (64-bit) addressing for node-to-node connectivity. The selection of the type of addressing to be used is defined in the IEEE 802.15.4 frame header, which indicates the type of addressing that is being used, both for the source and the destination. This address allows each device to identify itself within the PAN personal area network. The coordinating node is able to assign the addresses to the other devices within the PAN network that are within its coverage area. The extended address is an identifier that each device has and is known as an IEEE address, which by analogy is compared to the MAC address of Ethernet systems.
2.1 Dynamic Allocation of Global Addresses
To perform the dynamic allocation of global addresses in the wireless network of multiple hop sensors, with fixed nodes that form a tree-type topology, we are going to use the addressing that is contemplated within the IEEE 802.15.4 standard.
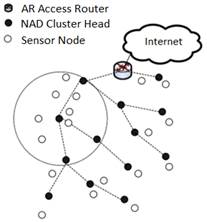
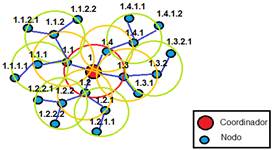
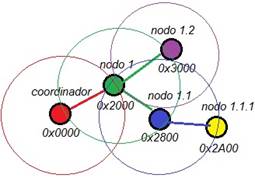
In our proposal, the cluster head node is defined as an address assigning node, which is in charge of assigning addresses to the nodes that are within its coverage area, it is represented as NAD., where i represents the node position within the multi-hop path in the tree topology Figure 2. The AR access router, represented as NAD., is the node that acts as a bridge to interconnect the internet network to the wireless sensor network and is known as the root node.
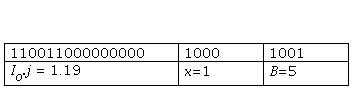
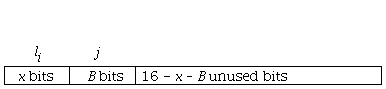
The NAD. node assigns addresses to the nodes that are within its coverage area and its address that has an I. value represented in . bits, this is taken as the basis for creating the address to assign to the nodes that have requested it be part of the network. If the number of nodes that have requested an address from the NAD. node is ., the NAD. node calculates the number of . bits, necessary to create the required addresses using the following expression:
B = Log2 n
The address assigned to the node is represented as I... where . < . < n-1. In this way, the assigned address will have a length of (. + .) bits and will be part of the 16 or 64 bits associated with short or extended addressing.
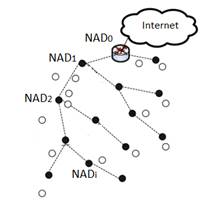
The NAD. node, which has an I. address, sends a unicast frame with the information contained in 3 bytes, if the address is short or 10 bytes if the extended address Figure 3, information that is part of the data (payload) of the IEEE 802.15.4 frame.
The information sent contains the new node address, the values of . and ., so that the node requesting its address can recognize its new address, the address of the head of the cluster and the number of bits available to assign to new nodes in case it acts as a NADi+1 address allocator node. In this way, the NADi+1 node, when it retransmits a frame sent to the Internet, sends it to the NAD. node so that it reaches the AR node and therefore to its destination, in the same way, the node is able to know the range of addresses assigned to the nodes that are part of the coverage area of the NAD. cluster head node. In conditions of high node density, a node may have multiple NAD. nodes available, with addresses to assign. In the unlikely event that the NAD. node has no leftover addresses, the node is responsible for requesting a new reassignment of addresses to its NADi-1 group leader and thus allowing the entry of a new node.
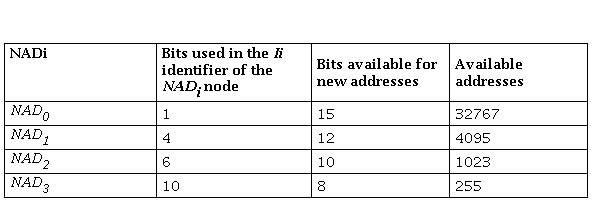
Initially the node NAD., is configured to have an address of value I. =1. The NAD. node sends a broadcast type frame to the nodes that are within its coverage range, indicating that it is ready to assign addresses. Later, the NAD. node receives the requests from the sensor nodes that need to be part of the network and therefore an address. If short addressing is used, the NAD. node has 15 bits to create addresses. If the number of nodes that require an address is . = 18, the number of bits required is . = 5 and work with a short address, in case the node NAD. assigns the value . = 19, it will send the following information: training the node requesting the address Figure 4.
In case the address is a short address Figure 5, the 16 bits are made up of:
During the address allocation process, it may happen that a sensor node is within the coverage area of several NAD. nodes. The IEEE 802.15.4 protocol specifies that a radio's PHY layer must provide an 8-bit integer value as an estimate of the received signal power when the frame is received. This value is known as the Received Signal Strength Indication (RSSI) This value is used to select the closest NAD. node, and will store the other addresses of the other NAD. nodes that also emitted the broadcast to have them as backup nodes, when the NAD. node that assigned the address is not operating and thus request a new address and have a new node that allows it to reach the AR node. Once the nodes have received the Ii.j address of the NAD. node, each one operates as NADi+1 to search for nodes within its coverage área.
The algorithm that determines the operation of a node is presented below. All nodes that are part of the infrastructure will run the same code.
Algorithm: Pseudo-code for our proposal
______________________________________________________________
1 Input: Ii NADi address, Ii_s source address request node
2 If address-allocator-node = true then
3 If available addresses = true then
4 Calculates how many bits it has to assign addresses
5 NADi node send broadcast frame (ready to assign address)
6 while frame received then
7 if allocation request then
8 Store Ii_s
9 Determine the number of requests
10 Calculate the value of . and .
11 Calculate addresses to assign
12 Assign new address Iij to node Ii_s
13 Send the new address to the nodes
14 Awaiting confirmation of successful assignment
15 else
16 exit
17 endif.
18 else send “addresses not available”
19 exit
20 endif
21 else
22 Request new address
23 if several nodes answer then
24 stores their addresses
25 selects the closest NADi node based on the received power.
26 endif
27 Request new address.
28 Receives the frame with the new address.
29 Update address.
30 Confirms change of address to the NADi node.
31 address allocator-node = true
32 endif
Table 1 presents an example of the number of addresses available when you have a tree network with a maximum of 4 NAD nodes that form one of the possible branches of the multi-hop network. If we consider the maximum range of 70 meters for each node, defined in the IEEE 802.15.4 protocol, the maximum coverage area of the network would have a radius of 280 meters, an area in which thousands of nodes should be in order to occupy all the possible directions.
As a result, Figure 6, a tree like topology is formed product of automatic address assignment.
3. Results
The RCB256RFR2 (ATMEL, 2013a) module Figure 7 used in the network prototype, allows to directly manage the link layer and directly manipulate the frame header of the IEEE 802.15.4 protocol. It is made up of an 8-bit microcontroller, ATMega256RFR2 from Atmel, it is powered by AAA batteries.
For the radio frequency part, the RCB256RFR2 module has a transceiver that operates at 2.4GHz and is compatible with the IEEE 802.15.4 standard. For the development of the algorithm for automatic addressing and definition of the topology, using the IEEE 802.15.4 standard, we use the development software ASF® (Atmel Software Framework) (ATMEL, 2013b) proposed by the manufacturer Atmel ™, which has a set of the libraries that facilitate code creation and programming, the most important is the Wireless Composer Development tool (Microchip, 2016) that allows systems to be easily evaluated and tested using the Atmel Studio.
In each sensor node, the proposed algorithm was implemented. To demonstrate the address allocation dynamically, the creation of the tree type topology and the correct operation of the NAD. nodes, IEEE 802.15.4 frame capture software was used, which provides us with the necessary information for verification.
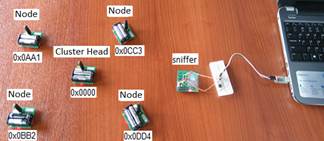
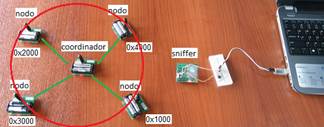
The nodes operate with the IEEE 802.15.4 standard working in no beacon mode, using the Carrier Sense Multiple Access with Collision Avoidance (CSMA-CA) access method. In the event that there are failed links or errors in the transmission, the CSMA-CA protocol solves the problem by configuring the nodes to retransmit the frame in the event that a confirmation that the frame arrived successfully (acknowledge ACK) is not received. In the tests, five RCB256RFR2 modules were used, the module that works as NAD. is initialized with the address 0x0000, the remaining four modules will fulfill the role of sensor nodes that require an address to be assigned to be part of the wireless sensor network and after they have already assigned their address, these nodes start assigning addresses to the nodes that are within their coverage area.
3.1 Start Topology
In this scenario, all sensor nodes are within the coverage area of the NAD. node Figure 8, the nodes are within the coverage area of the NAD. node, and the sniffer node is positioned in a position that can capture the frames of all nodes. The nodes are initialized with the following random addresses 0x0AA1, 0x0BB2, 0x0CC3 and 0x0DD4.
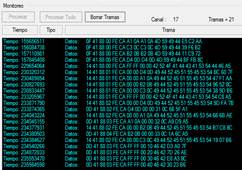
The moment the nodes are switched on the node NAD. sends a broadcast frame Figure 9. The header of the IEEE 802.15.4 frame begins to the right of the graph and the Little-endian rule is used for its interpretation the payload of the frame can be identified without difficulty. As you can see, the first four frames indicate the sequence with which the nodes were turned on, the fifth frame is that of the coordinator when sending the broadcast, this frame is the one that begins the assignment of the new addresses.
The time is measured in microseconds and the time elapsed since the NAD. node sends the broadcast frame, at time "229654064" until it sends the last unicast frame with the last address to be assigned at time "235564598", indicates that the time required for the 4-node star network to be operational is 5.9 seconds. Performing a projection of more than 4 nodes, we can deduce that the time to assign identifiers to 1000 nodes is 1475 seconds.
In this way, the star type topology is formed Figure 10 having as node root of the topology the node NAD. and the nodes with the new assigned addresses.
3.2 Tree Topology
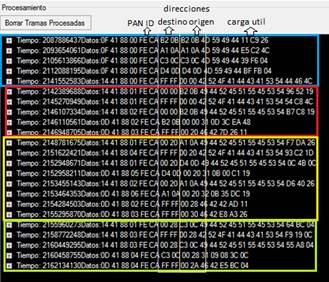
In this scenario, the nodes were placed in such a way to have a multi-hop network and form a tree-like topology. The nodes were configured to have a coverage area with a radius of 14 meters. The nodes that are closest to the NAD0 node were located at a distance of approximately 10 meters, the farthest nodes were located at 20 meters, in order that they are outside the coverage range of the node and do not receive the broadcast sent by this node. In the section marked in blue, you can see the first four initial frames of the nodes, this shows the sequence of how the nodes were turned on. The source and destination addresses must be interpreted from right to left, the fifth frame corresponds to the broadcast type frame made by the coordinator once switched on.
The section marked with yellow Figure 11, shows that node 0x0AA1 responds to the broadcast of node NAD. with address 0x2000, resends the broadcast this time node 0x0DD4 responds and also to node 0x0AA1.
The node assigns the following addresses 0x2800 and 0x3000 to the nodes respectively, as seen in the last two lines of this section, each of these nodes becomes NAD nodes and sends the broadcast once they have been assigned addresses. Finally, the section marked in green shows that the last node 0x0CC3 that has not yet been assigned the address responds to the first broadcast sent by address 0x2800 and this node assigns it address 0x2A00. Once assigned its address, the process repeats at each node.
As a result of executing our algorithm, a hierarchical addressing was obtained and a tree-like topology was formed as shown in Figure 12.
5. Conclusions
The need for more dynamic and capable solutions in the Industry 4.0 field, has contributed to increase applications require low delays and long operating times from the WSN.
This document demonstrates that it is possible to adapts the IEEE 802.15.4 standard in a simple way to have global auto configuration. The link level identifiers are used as global identifiers. It is shown that, with the assigned addresses, the tree type topology is formed, which allows each node to know which is the next node to send the frame to so that it reaches the root node without using processes at the network-layer.
Our proposal, use address allocation schemes, cluster based. The nodes maintain allocation states to determine the availability of addresses to assign to a new node that connects to the network. The hierarchical assignment guarantees the assignment of unique global addresses. Currently, we are working on the development of a routing protocol based solely on the link level for wireless sensor networks.